hInjector
Update: This tool is no longer maintained and supported.
hInjector
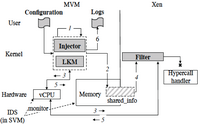
hInjector is a tool for injecting hypercall attacks in virtualized environments for the purpose of evaluating hypercall security mechanisms - intrusion detection systems and mandatory access control mechanisms. hInjector injects hypercall attacks during regular operation of guest virtual machines, crafted with respect to representative attack models. The current implementation of hInjector is for the Xen hypervisor, which can be ported to other open-source hypervisors, such as KVM.
For more information, please contact Aleksandar Milenkoski.
Links:
Mailing List
Publications
-
Towards Testing the Software Aging Behavior of Hypervisor Hypercall Interfaces. in 2019 {IEEE} International Symposium on Software Reliability Engineering Workshops ({ISSREW}) (2019).
-
Towards Testing the Performance Influence of Hypervisor Hypercall Interface Behavior. in Proceedings of the 10th Symposium on Software Performance 2019 (SSP’19) (2019).
-
{Evaluation of Intrusion Detection Systems in Virtualized Environments Using Attack Injection}. in The 18th International Symposium on Research in Attacks, Intrusions, and Defenses (RAID 2015) (2015).
-
{Experience Report: An Analysis of Hypercall Handler Vulnerabilities}. in {Proceedings of The 25th IEEE International Symposium on Software Reliability Engineering (ISSRE 2014) --- Research Track} (2014).
-
{Technical Information on Vulnerabilities of Hypercall Handlers} (2014).
-
{HInjector: Injecting Hypercall Attacks for Evaluating VMI-based Intrusion Detection Systems}. in The 2013 Annual Computer Security Applications Conference (ACSAC 2013) (2013).
-
{Towards Benchmarking Intrusion Detection Systems for Virtualized Cloud Environments}. in Proceedings of the 7th International Conference for Internet Technology and Secured Transactions (ICITST 2012) (2012). 562–563.